Information Security Policy
Overview
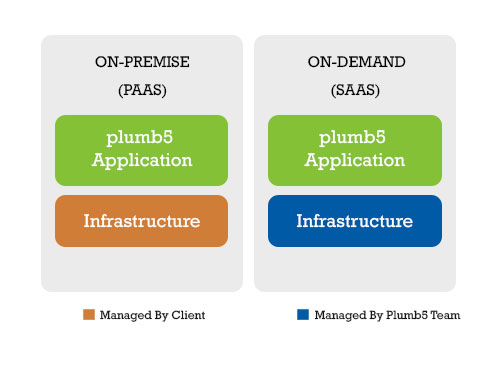
Plumb5 offers both On-demand(SaaS) and On-Premise(PaaS). Technical and organizational security and privacy measures are implemented for each type of offering in compliance with Decisive Analytical Systems policy according to its architecture, intended use, and the type of service provided. Figure 1 provides an illustration of the general division of responsibility within each service type.
In a On-Premise model,the client or their preferred Vendor manage the infrastructure. Plumb5 team would create, deploy, and manage the application.
In a On-Demand Model Plumb5 team would be managing both infrastructure and the platform. The infrastructure - cloud services are with renowned providers like AWS and Azure.
This Data Security and Privacy Principles document describes the Decisive Analytical Systems policies and practices.
Governance
Decisive Analytical Systems security policies, which derive their authority from specific corporate instructions, are established and managed by the the organization and are an integral part of our business. Compliance with internal IT policies is mandatory and audited.
Security Policies
Decisive Analytical Systems information security policies are reviewed at least annually and refined as necessary to keep current with modern threats and in line with updates to broadly accepted international standards.
Decisive Analytical Systems follows a mandated set of employment verification requirements for all new hires, including supplemental employees. The requirements, which may be subject to change, include, but may not be limited to, criminal background checks, proof of identity validation, and additional checks if the candidate previously worked for a government entity. Decisive Analytical Systems company is responsible for implementing the above requirements in its hiring process as applicable and permissible under local law.
Security incidents are handled in accordance with Decisive Analytical Systems incident management and response policies, taking into account data breach notification requirements under applicable law.
The core functions of Decisive Analytical Systems cybersecurity incident management practice are conducted by our Infrastructure Team. This team coordinates with other functions within Decisive Analytical Systems to investigate suspected incidents, and if warranted, define and execute the appropriate response plan. Upon determining that a security incident has occurred, Decisive Analytical Systems will promptly notify affected cloud services clients as appropriate.
Access, Intervention, Transfer and Separation Control
The architecture of Decisive Analytical Systems services maintains logical separation of client data. Internal rules and measures separate data processing, such as inserting, modifying, deleting, and transferring data, according to the contracted purposes. Access to client data, including any personal data, is allowed only by authorized personnel in accordance with principles of segregation of duties, strictly controlled, and monitored in accordance with Decisive Analytical Systems internal privileged user monitoring and auditing.
Decisive Analytical Systems privileged access authorization is individual, role-based, and subject to regular validation. Access to client data is restricted to the level required to deliver services and support to the client (i.e., least required privilege).
Transfer of data within Decisive Analytical Systems network takes place on wired infrastructure and behind firewalls, without the use of wireless networking. Upon request or service termination, pursuant to the terms of the cloud service agreement, client data is rendered unrecoverable in conformity with guidelines for media sanitization.
Service Integrity and Availability Controls Decisive Analytical Systems cloud services undergo penetration testing and vulnerability scanning prior to production release. Additionally, penetration testing, vulnerability scanning, and ethical hacking is performed by Decisive Analytical Systems and authorized independent third parties, if required.
Modifications to operating system resources and application software are governed by Decisive Analytical Systems change management policies. Changes to network devices and firewall rules are also governed by the change management policies and are separately reviewed by security staff prior to implementation.
Service Integrity and Availability Controls
Decisive Analytical Systems cloud services undergo penetration testing and vulnerability scanning prior to production release. Additionally, penetration testing, vulnerability scanning, and ethical hacking is performed by Decisive Analytical Systems and authorized independent third parties.
Modifications to operating system resources and application software are governed by Decisive Analytical Systems change management policies. Changes to network devices and firewall rules are also governed by the change management policies and are separately reviewed by security staff prior to implementation.
Activity Logging and Input Control
Decisive Analytical Systems policy requires administrative access and activity in its cloud services’ computing environments to be logged and monitored, and the logs to be archived and retained in compliance with the management plan.
Changes made to production cloud services are recorded and managed in compliance with Decisive Analytical Systems change management policy.
Physical Security and Entry Control
Decisive Analytical Systems maintains physical security standards designed to restrict unauthorized physical access to resources. Entry points into Decisive Analytical Systems data centers are limited, controlled by access readers, and monitored. Access is allowed only by authorized personnel.
Delivery areas where unauthorized persons may enter the premises are strictly controlled. Personnel who are not part of the operations, facilities, or security staff are registered upon entering the premises and are escorted by authorized personnel while on the premises.Terminated employees are removed from the access list and required to surrender their access badges. Use of access badges is logged.
Order Control
Data processing is performed according to offering agreement in which Decisive Analytical Systems describes the terms, functionality, support, and maintenance of a cloud service offering and measures taken to maintain the confidentiality, integrity, and availability of client data.
Compliance
Decisive Analytical Systems information security standards and management practices for cloud services are aligned to global standard for information security management. Assessments and audits are conducted on need basis by Decisive Analytical Systems to track compliance with its information security standards.
Third Party
Decisive Analytical Systems cloud services may require third party to access client data in normal performance of their contracted duties. If such a third party sub processor is engaged in the delivery of a cloud service, the sub processor and its role will be provided upon request. Decisive Analytical Systems requires all such sub processors to maintain standards, practices, and policies which preserve the overall level of security and privacy provided by Decisive Analytical Systems.
Best Practices
- Security Policy
- Separation of Duties
- Data Classification
- User Identification
- Password Controls
- Authorization / Access Control
- Role-based Access Control
- Directory Integration
- Row and Column-level Security
- Network Traffic Encryption
- Data Encryption
- Backup Media Protection
- Residual Information Protection
- Secure Zone
- Operating System Security
- Vulnerability Management
- Physical Security
- Security Process Audit
- Business Continuity Plans
Incident Response Plan
Introduction
In accordance with industry ‘best practices’ and to comply with numerous compliance regulations, Decisive Analytical Systems has implemented various procedures, policies and guidelines in order to protect the confidentiality, integrity and availability of their critical client data and their computing resources. This Incident Response Plan is one such procedural document intended to prepare Decisive Analytical Systems to address security incidents. Regular testing and refinement of this plan will help Decisive Analytical Systems prepare for adverse security incidents and ultimately help them to manage and minimize risk.
It is anticipated that as new technologies and new requirements are introduced this document will need to be modified and should be reviewed at least annually.
Overview
There are many different security incidents that can occur with assorted severity levels and not all incidents will require focus on each step. However it is important to be prepared and understand that typically different phases exist in responding to an incident, and the goals and objectives of each phase. The different phases of a security incident response plan at Decisive Analytical Systems are as follows:
- Prepare
- Identify
- Contain
- Eradicate
- Recover
- Review
Prepare
In preparing for security incidents several items would be addressed.
- Incident handling team would include security officers, system analysts and human resources personnel
- End users and analysts are trained at an appropriate level. Login banner and warning messages would be posted.
-
Contact information is included as an appendix to this document and should be available in hard
copy for:
- personnel that might assist in handling an incident
- key partners who may need to be notified
- business owners to make key business decisions
- outside support analysts with security expertise
- Backups should be taken and tested
Identify
Awareness that a security incident has occurred can originate from different sources such as technical people, end users or even clients.
Best practices suggests to declare that an incident has occurred when security officers’ sense that an adverse risk to the company exists and then assemble the team and implement the plan. It is also suggested to early on have multiple people involved, to save all key system files or records such as log files and start detailed documentation as soon as possible.
Ultimately business owners need to be involved in many security incidents to decide what are the goals in handling a particular incident, such as immediate business recovery or forensic examination.
Contain
Following basic procedures can contain many incidents. Specific procedures will frequently depend on the nature of the incident, as well as the direction of the business owner.
- Obtain and analyze as much system information as possible including key files and possibly a backup of the compromised machine for later forensic analysis.
-
If one machine has been exploited others might be vulnerable. Actions that might need to be
taken on a large scale might include:
- Download security patches from vendors
- Update antivirus signatures
- Close firewall ports
- Disable compromised accounts
- Run vulnerability analyzers to see where other vulnerable hosts are
- Change passwords as appropriate
Eradicate
To eradicate the problem specific procedures will frequently depend on the nature of the incident as well as the direction of the business owner. Key considerations would include:
- If machines OS has been compromised it needs to be rebuilt using hardened machines on appropriate platforms
- Test any backups prior to restore and monitor for a new incident.
- Document everything.
Recover
The recovery phase goal is to return safely to production. Once again specific actions might depend on the nature of the incident as well as the direction of the business owner. Key considerations include:
- Retest the system preferably with a variety of end users.
- Consider timing of the return to production.
- Discuss customer notification and their concerns
- Discuss media handling issues
- Continue to monitor for security incidents
Review
This phase is to allow Decisive Analytical Systems to better handle future security incidents. A final report would be written describing the incident and how it was handled using the Incident reporting form. Suggestions for handling future incidents and reworking this document should be included in this report.
Contact information
Personnel that might assist in handling an incident
- Rashid Dawood
Business owners to make key business decisions
- Rashid Dawood (CPO)
- Vijay Chander S (CEO)
Last Modified: 1st January 2021